Please note that all submissions to the site are subject to the wiki's licence, CC 4.0 BY-SA, as found here
Bambu Lab Authorization Control System: Difference between revisions
Linking, copy editing, removing extra references list, etc. |
How to decrypt and reverse engineer Bambu Connect Tags: Reverted Visual edit: Switched |
||
| Line 135: | Line 135: | ||
https://www.reddit.com/r/BambuLab/comments/1i4vp5i/comment/this/ | https://www.reddit.com/r/BambuLab/comments/1i4vp5i/comment/this/ | ||
== Reverse Engineering Bambu Connect == | |||
Bambu Connect is an Electron App with Security through Obscurity priciples, hence it is inherently insecure. To read the main.js for further analysis or extracting the private key stored by Bambu in the app: | |||
# Use the MacOs .dmg file, not the exe. Finding the needed decryption code is easier in the .dmg | |||
# Extract ''bambu-connect-beta-darwin-arm64-v1.0.4_4bb9cf0.dmg''<ref>https://public-cdn.bblmw.com/upgrade/bambu-connect/bambu-connect-beta-darwin-arm64-v1.0.4_4bb9cf0.dmg</ref>, in there you can find the files of the underlying Electron app in ''Bambu Connect (Beta).app/Contents/Resources'' folder | |||
# The app uses asarmor to prevent easy reading, the key is stored in ./app.asar.unpacked/.vite/build/main.node and can be extracted. Unpacking app.asar without fixing it first will result in an encrypted main.js file and 100 GB of decoy files generated, don't try it. | |||
# Load main.node in Ghidra and Auto-Analyze it. Then search for the GetKey function, or press G and go to 0000b67e<ref>https://www.reddit.com/r/OrcaSlicer/comments/1i2t6l8/comment/m7tuf2i/</ref> | |||
# Write down the hex key, for this build it's B0AE6995063C191D2B404637FBC193AE10DAB86A6BC1B1DE67B5AEE6E03018A2 | |||
# Install the npm package asarfix and use it to fix the archive: <code>npx asarfix app.asar -k B0AE6995063C191D2B404637FBC193AE10DAB86A6BC1B1DE67B5AEE6E03018A2 -o fixed.asar</code> | |||
# Now you can extract it in cleartext with <code>npx asar extract fixed.asar src</code> | |||
# ./src/.vite/build/main.js is minified, use any JavaScript beautifier to make it better readable. Interesting user code including the private key is at the end of the file. | |||
=== Extracting certs and private key === | |||
The private key and certs are further obfuscated, to get cleartext you need to do: Encrypted string from cy() -> ure(string, key) -> RC4 decryption -> decodeURIComponent() -> final string. | |||
Example Python reimplementation to extract the secrets, easy to run. Copy the content of t from function cy() in main.js and paste it here. After running, you have a private key from Bambu Lab. | |||
<code>☁</code> | |||
== Community tools and scripts == | == Community tools and scripts == | ||
Revision as of 16:55, 19 January 2025
On January 16, 2025, the 3D-printer manufacturer Bambu Lab announced that future firmwares for their 3D printers would introduce an authorization and authentication protection mechanism for their connection and control, in the name of security. Bambu has stated the following:
"This change is mitigating any risk of remote hacks or printer exposure issues that have happened in the past and also lower the risk of abnormal traffic or attacks."[1][2]
Controversy regarding firmware updates
Potential for remote disabling of printers
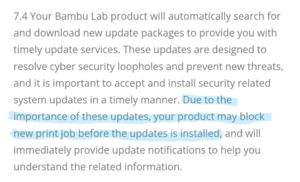
A significant concern raised by the community revolves around the wording in Bambu Lab's Terms of Service and firmware update announcements. Critics and users argue that the phrasing leaves open the possibility for the manufacturer to remotely disable printers that are not updated to the latest firmware. Specifically, Bambu Lab's Terms of Service[3] states that printers may block "new print jobs" if updates are not applied, which some users interpret as a potential pathway for forced obsolescence.[4] The announcement, however, specifically says, "What happens if I never upgrade to this firmware? You may continue using an older firmware version that does not include the new security updates; however, this means the printers may miss out on important security fixes or bug patches included in newer versions."[5]
While defenders of Bambu Lab point out that offline modes such as SD-card printing and LAN-only setups would remain functional, others point out that the Terms of Service do not explicitly limit this restriction to cloud-based printing. This ambiguity has led to speculation that Bambu Lab could enforce broader limitations, effectively rendering printers inoperable for users who choose not to update.[6]
Debate over "bricking" terminology
The debate has also extended to the definition of "bricking." Some community members assert that if a printer is unable to accept new print jobs without an update, it effectively becomes non-functional and qualifies as being "bricked." Others counter that as long as certain offline functionalities remain (such as SD-card printing) the term does not accurately apply.[7]
Community Strategies to Deal with Risks
Users have discussed strategies to avoid possible disruptions, including:
- Operating printers exclusively in offline modes.
- Utilizing LAN connections or VPN setups: this requires an access key from the printer (previously, you could use your cloud credentials over LAN).
- Exploring alternative firmware or third-party scripts to restore full functionality[8].
Bambu Lab's justification and rebuttal
Bambu Lab has stated that the authorization system is in place in order to protect against "remote hacks," "printer exposure," and "abnormal traffic or attacks." There are, however, several ways to mitigate these risks without the loss of user control that their system causes:
- The "remote hacks" that were cited as an example in the article seem to be a direct result of the 3D-printer vendor not responding properly to a reported security vulnerability in their product.[9] Therefore, in order to get attention, the researcher decided to infect machines and display a harmless message to spread publicity. Properly responding to security vulnerabilities, working to patch them quickly, and working with the security community (who would be more than happy to help secure products) would be some ways to prevent this.
- In the article cited about printer exposure, the hack was carried out largely because of user misconfiguration.[10] Printer exposure can be mitigated by offering more convenient ways to securely expose printers to the internet, so that users are not tempted to allow unauthenticated access over the network.
- The "abnormal traffic" can be mitigated by steps Bambu has already put in place, as detailed in their own article on the matter[11].
Issues with LAN mode requiring authorization
Bambu Lab printers have the ability to be controlled over both cloud and LAN. This allowed users to integrate their printers into private networks and maintain full control without having to rely on the manufacturer's server while also allowing cloud access. The new authorization system mandates that even LAN-based operations must go through an authentication process using Bambu Connect to retain full control.[12] Full local access is still possible and unchanged for those not using the cloud.
This change has drawn criticism for many reasons:
- Privacy concerns: Requiring authentication for LAN mode raises concerns about data being unnecessarily exposed to Bambu Lab's servers, even for local-only operations, though previously, the printer was also connected and could be controlled by the cloud even when sending prints locally.
- Loss of offline independence while also using cloud: Before, users could have hybrid offline setups. The requirement for authentication removes this option unless users revert to older firmware versions, which Bambu does not allow people to do once they have updated to the firmware using the new scheme.
- Increased complexity: The added authentication layer complicates workflows for users who built custom setups or relied on third-party integrations for LAN control while retaining cloud functionality[13].
Precedents and comparisons
Critics have likened this potential functionality to similar cases in other industries where manufacturers remotely restrict product features. Notable examples include HP's printer firmware updates that rendered third-party ink cartridges unusable and Tesla's software locks on second-hand vehicles. These parallels suggest a broader trend of manufacturers using software to control hardware capabilities post-purchase.[14][15]
Implementation Timeline and Requirements
The authorization system will be rolled out in phases, starting with the X1 series printers. A beta firmware (version 01.08.03.00) was released on January 17, 2025, with the full release scheduled for January 23, 2025. The P & A series printers will get similar updates at an unspecified future date.
To use printers with the new authorization system, users must update multiple pieces of software:
- Bambu Studio must be updated to version 01.10.02.64 or higher
- Bambu Handy mobile app must be updated to version 2.17.0 or higher
- The new Bambu Connect application must be installed for using third-party slicers
These software updates are mandatory for users who update their firmware. Failing to update all components simultaneously will result in certain printer controls becoming unusable. Users who choose to maintain third-party software compatibility can continue using older firmware versions, though this will not be an option for new printers, which will ship with the authorization system pre-installed.
Bambu Lab states these coordinated updates are necessary because the new authorization system fundamentally changes how the printer validates and accepts commands. The older versions of Bambu Studio and Bambu Handy lack the authentication mechanisms required to interact with printers running the new firmware. The Bambu Connect application was created specifically to provide a controlled interface for third-party software, replacing the previous direct access through network plugins[16].
Impact on third-party integration and user choice
Changes to third-party access
The new authorization system replaces direct network API access with a more limited URL-based interface through Bambu Connect. Third-party software can only interact with the printer by sending specific URL commands to Bambu Connect[17]. The interface requires three parameters:
path: The absolute file system path to the 3MF file (e.g., /tmp/cube.gcode.3mf)name: The name of the file (e.g., Cube)version: A fixed value of 1.0.0 for compatibility
A complete command must be formatted as:
<syntaxhighlight lang="text">
bambu-connect://import-file?path=%2Ftmp%2Fcube.gcode.3mf&name=Cube&version=1.0.0
</syntaxhighlight>
This interface only allows basic file transfer and print initiation. All other printer-control functions previously available to third-party software are now exclusive to Bambu's own applications. The path and name parameters must be URL-encoded using encodeURIComponent or equivalent functions[18].
Reduced home-automation capabilities
While basic status monitoring remains available (e.g., print-progress updates in Home Assistant), the new firmware removes the ability for home-automation systems to control printer functions. Users can no longer:
- Start or stop prints remotely using Home Assistant, BTT Panda Touch,[19] or other third-party accessories or software interfaces
- Control printer temperatures or cooling
- Automate printer behaviors based on sensor data or events
- Access camera feeds through third-party applications[20]
Permanent nature of the update
Once a printer is updated to the new firmware, users cannot revert to previous versions that allows full control of the printer using LAN mode access key while signed into the cloud[21]. The option still exists to disable the cloud service.
The manufacturer states this change is required for security, but community members note that many of the security vulnerabilities being addressed stem from Bambu's own cloud-centric design choices rather than inherent risks of local network control[22]. The update forces users into using Bambu Connect middleware if they want to retain cloud functionality.
This can be characterised as a significant post-purchase reduction in functionality for existing owners who bought their printers with the understanding they could use third-party software and home-automation tools, but also only affects users actively choosing to use Bambu Cloud at the same time. The inability to revert these changes, combined with the mandatory nature of the update for new printers, is used to demonstrate how manufacturers can use software updates to unilaterally modify the capabilities of hardware products after purchase, although in this case the changes affect only people already choosing to use the cloud service[23].
For users that would want to use a third-party slicer while using their cloud service, Bambu would require those users to download and install Bambu Connect in order to send gcode wirelessly over LAN or over the cloud. While Bambu claims that they were in contact with SoftFever, the developer of OrcaSlicer, as of writing, SoftFever still does not have any keys for Bambu Connect and the new firmware is only available as opt-in beta at the moment.[24]
Impact on functionality
While some functionality remains unauthenticated like in previous firmware versions (sending status information from the printer over the network, starting a print job using SD cards), the most important features now require authentication through a new closed-source client called Bambu Connect[25]. These restricted features include:
- Initializing prints via LAN or cloud mode
- Remote video access to monitor prints
- Controlling motion system, temperature, fans
- AMS settings and calibrations
- Home automation integration beyond basic status monitoring
Previously, third-party software such as OrcaSlicer[26] could interact with Bambu Lab printers via the open-source Bambu Studio and proprietary network plug-ins. While Bambu Connect provides a limited URL-based API to initiate prints, most functionality previously openly available is now restricted to Bambu's ecosystem[27].
Previously, third-party accessories such as Panda Touch would allow users to control their printers with a standalone device. Panda Touch was especially popular amongst P series printer owners since P series printers contain a monochromatic screen with a D-pad by default for printer control whereas Panda Touch is a full-color touch screen that had a small battery so that way users could reposition and detach their Panda Touch off their printers if needed. Users would be able to queue up jobs, jog printer motors, and connect to multiple printers at once in order to monitor print jobs. According to Big Tree Tech (BTT), the manufacturer of the Panda Touch, they urge users of Panda Touch not to update firmware any further since doing so would foreseeably permanently break compatibility with users' printers and their Panda Touch. [19]
Communication with Panda Touch developers
As of writing, no formal communication has happened between Big Tree Tech (BTT), the manufacturer and developer of Panda Touch, and Bambu Labs. Based on their Facebook announcement, BTT stated that they have reached out to Bambu and will update if Bambu responds to their correspondence. [19]
Communication with OrcaSlicer developers
Before the official announcement of the new authorization and authentication, Bambu Lab engaged with the OrcaSlicer development team regarding the changes. This communication has sparked significant discussion within the 3D-printing community, particularly regarding its timing, tone, and implications.
Pre-announcement contact
Reports from OrcaSlicer demonstrate that Bambu Lab provided limited advance notice of the changes that would render their software incompatible with Bambu printers running the new firmware. The communication emphasized:
- The introduction of Bambu Connect as the only supported method for interacting with third-party slicers.
- The discontinuation of the network plugin API that OrcaSlicer and other tools relied on for printer control.[28]
- An invitation for OrcaSlicer developers to adapt their software to integrate with the Bambu Connect URL scheme.
The communication lacked the detailed technical documentation that would be necessary for developers to be able to work with the new requirements.
How the community viewed these actions
This approach has been interpreted by many as a calculated move by Bambu Lab to enforce tighter control over its ecosystem. Primary criticisms of Bambu were:
- Lack of transparency: The limited warning to OrcaSlicer devs suggests that Bambu Lab prioritized internal rollout schedules over community engagement with existing customers. Point to the contrary: The new firmware is in beta and Bambu Connect middleware contains temporary compomises to allow third-party slicers to work as before.
- Lack of follow-through: As of writing, SoftFever, OrcaSlicer's lead developer, still does not have API keys for Bambu Connect, a necessary layer of Bambu software that would need to be integrated into OrcaSlicer. Bambu's original announcement prominently mentioned OrcaSlicer and gave the impression that Bambu is actively providing the necessary assets so that SoftFever would be able to implement the new software architecture so that OrcaSlicer users are able to still use OrcaSlicer to send gcode to their printers without needing Bambu Connect to be installed as a separate program. The lack of active cooperation does not reflect favorably upon Bambu as it seems like their announcement used OrcaSlicer's name to try to make it seem like Bambu is trying its best to make sure that developers have what they need, but in reality, their inaction seems to show that Bambu is not making a sincere attempt to ensure that OrcaSlicer remains supported. [24]
- Disregard for open-source collaboration: OrcaSlicer is widely used in the community; it is an open-source effort to improve the 3D-printing experience for all customers. By abruptly altering the compatibility landscape, Bambu Lab is seen as undermining good-faith initiatives to improve the ecosystem for everyone. The decision to restrict network APIs in favor of proprietary systems such as Bambu Connect represents a broader industry trend of closing off ecosystems that were once open, removing customer choice, privacy, and freedom.
- Token support for third-party tools: While Bambu Connect provides a workaround for third-party slicer use, it significantly restricts functionality and complicates workflows, leading many to question the sincerity of Bambu's stated support for open-source tools.[29]
- Power imbalance: As the hardware manufacturer, Bambu Lab has the ability to dictate how its products can be used; often to the detriment of third-party developers and users.
Community-driven workarounds and technical alternatives
The 3D-printing community has begun exploring potential workarounds to restore functionality and user autonomy. These efforts focus on bypassing or mitigating the limitations imposed by the firmware update.
Custom firmware development
Discussions within the community highlight interest in developing custom firmware as an alternative to Bambu's official updates. One prominent project mentioned in forums is the development of custom firmware for the X1-series printers, such as the "X1Plus Custom Firmware."[30] This firmware aims to:
- Restore direct network control and third-party slicer compatibility.
- Re-enable previously available features such as motion-system adjustments, temperature control, and AMS settings without requiring proprietary software.
- Provide users with greater flexibility in integrating printers with home-automation systems and workflows.
However, custom firmware development faces significant challenges, including:
- Limited documentation and proprietary hardware components, which complicate reverse-engineering efforts.
- The potential voiding of warranties and risks of bricking devices.
- Legal concerns regarding intellectual property and bypassing manufacturer-imposed restrictions.
LAN mode and blocked internet access
This is a guide made by the user Tzeny15
https://www.reddit.com/r/BambuLab/comments/1i4vp5i/comment/this/
Reverse Engineering Bambu Connect
Bambu Connect is an Electron App with Security through Obscurity priciples, hence it is inherently insecure. To read the main.js for further analysis or extracting the private key stored by Bambu in the app:
- Use the MacOs .dmg file, not the exe. Finding the needed decryption code is easier in the .dmg
- Extract bambu-connect-beta-darwin-arm64-v1.0.4_4bb9cf0.dmg[31], in there you can find the files of the underlying Electron app in Bambu Connect (Beta).app/Contents/Resources folder
- The app uses asarmor to prevent easy reading, the key is stored in ./app.asar.unpacked/.vite/build/main.node and can be extracted. Unpacking app.asar without fixing it first will result in an encrypted main.js file and 100 GB of decoy files generated, don't try it.
- Load main.node in Ghidra and Auto-Analyze it. Then search for the GetKey function, or press G and go to 0000b67e[32]
- Write down the hex key, for this build it's B0AE6995063C191D2B404637FBC193AE10DAB86A6BC1B1DE67B5AEE6E03018A2
- Install the npm package asarfix and use it to fix the archive:
npx asarfix app.asar -k B0AE6995063C191D2B404637FBC193AE10DAB86A6BC1B1DE67B5AEE6E03018A2 -o fixed.asar - Now you can extract it in cleartext with
npx asar extract fixed.asar src - ./src/.vite/build/main.js is minified, use any JavaScript beautifier to make it better readable. Interesting user code including the private key is at the end of the file.
Extracting certs and private key
The private key and certs are further obfuscated, to get cleartext you need to do: Encrypted string from cy() -> ure(string, key) -> RC4 decryption -> decodeURIComponent() -> final string.
Example Python reimplementation to extract the secrets, easy to run. Copy the content of t from function cy() in main.js and paste it here. After running, you have a private key from Bambu Lab.
☁
Community tools and scripts
In addition to firmware alternatives, some users have come up with custom scripts and software tools to interface with Bambu Lab printers indirectly. These tools often rely on:
- Reverse-engineering the URL-based commands required by Bambu Connect to enable partial functionality with third-party slicers like OrcaSlicer.
- Creating local server emulations to replicate the network API previously available before the update.
While these tools provide temporary solutions, they don't fully replace the open ecosystem that existed prior to the authorization update.
Re-engineering printer-control electronics
ChazLayyd's Bambu Lab Klipper Conversion project is currently in an incomplete stage[33][34]. While the project was not made in response to Bambu's announcement, there has been a wave of new public interest in this specific project. ChazLayyd's documentation instructs P1S owners to non-destructively remove the old control electronics that run Bambu's proprietary software and instructs P1S owners to install off-the-shelf control components so that the existing motor connectors and other critical electronics can communicate with the newly-installed off-the-shelf control components.
Advocacy for open-ecosystem support
Community members have also organized to advocate for open-source support and rollback options. Suggestions include:
- Allowing an opt-out option for existing users who prefer local network control without cloud dependency.
- It should be pointed out that this has always been possible and past firmware updates made signing into the cloud at any point completely unnecessary. This information continues to be ignored by some.
- Providing an official API for third-party slicers under specific licensing agreements that allow secure authorized usage.[35]
Bambu corporate strategy vs maker community values
Impact on professional users and print farms
The restrictions imposed by the new authorization system create significant operational challenges for professional users who kept their printers signed into the cloud:
- Print farms can no longer use custom automation systems to manage multiple printers
- Workflows built around third-party software have to be completely redesigned
- The requirement to manually export and import files through Bambu Connect creates additional labor
- Integration with existing business systems and workflows becomes more difficult or impossible
- Professional users with more than 20 printers report the new workflow as "an absolute nightmare"[36]
The solution to the above is not to sign the printer into the cloud. Keeping the printer signed in would be a security oversight in this use case on the part of the print farm.
Privacy and data-collection concerns
The shift toward mandatory use of Bambu's software ecosystem raises several privacy and data collection concerns:
- All printer operations must now pass through Bambu's cloud infrastructure when using cloud mode
- User print data, including file names and print settings, becomes visible to Bambu when cloud is used
- Camera feeds and operational data are processed through Bambu's servers while on a different network
- Users have limited visibility into how their data is collected, stored, and used in the cloud
- The system creates dependence on Bambu's cloud services availability for basic printer functionality[37]
While Bambu Lab maintains that cloud processing is necessary for security and functionality, community members argue this represents unnecessary data collection that could be handled locally.[38] The company's cloud infrastructure costs are significant, leading some users to speculate that future monetization of the cloud services may be planned.[39] Therefore, people should assess if their use case mandates the use of the cloud service and disable it when it doesn't.
This shift from local control to cloud-dependent operation is part of a broader trend in consumer devices, where manufacturers use security concerns to justify increased data collection and reduced customer control over devices they bought and paid for. Privacy-conscious users should operate their printers in LAN-only mode to avoid cloud connectivity.
Customer reactions
Customer reactions have been overwhelmingly negative.[40][41] Bambu Lab has historically pushed cloud-based printer interaction while offering limited LAN mode functionality.[42] Many customers argue that the security issues this locked-down firmware claims to address are actually consequences of the company's cloud-based design choices rather than inherent risks of local network control,[43] which continues to infuriate users who are now told that security is the justification for a loss of freedom. As a result of the announcement of the shift, customer ratings on sites like Trustpilot rapidly dropped,[44] with many reviews citing the restrictions as the reason for the bad reviews.
The shift raises privacy concerns as user print data, including file names, print settings, and camera feeds, must now pass through Bambu's cloud infrastructure.
Many community members and customers ask whether the significant costs of maintaining and deploying this cloud infrastructure might lead to future monetization of these now-mandatory services,[45] with subscriptions required for features that once worked with local access.
It should be noted, however, that so far no changes have been made or indicated for those not using the cloud service. Past firmware updates made it possible to avoid using the cloud service completely by allowing pairing the slicer via IP address and access key and doing offline firmware updates without having to sign the printer into the service, not even temporarily, keeping local functionality unchanged.
Comparisons to similar practices by other companies
Bambu Lab's new authorization and authentication requirements have been compared to a number of practices by traditional printer manufacturers, such as HP or Epson, who have also faced backlash around their handling of digital-rights management (DRM)[citation needed ]. These comparisons address:
- Forced updates: Firmware updates have rendered third-party ink cartridges incompatible, forcing users to purchase proprietary consumables.
- Restricted features: Scanner/printer combos that will not scan if the ink is empty.
- Consumer backlash: Users criticized these updates as anti-consumer, with some pursuing class-action lawsuits for deceptive practices.[46]
Like 2D printers, Bambu Lab's update restricts functionality previously available to users and pushes them toward proprietary software and cloud-based control.
A parallel specific to the 3D-printing industry can also be drawn from the now-defunct 3D-printer manufacturer MakerBot, whose shift from open-source, DIY-focused machines in 2012 to closed-source, proprietary machines (similarly to Bambu Labs), ultimately driving customers to less-expensive, open-source competitors.[47] MakerBot was also accused of asserting ownership over publicly available, open-source designs uploaded to its 3D print repository, Thingiverse.[48] These factors contributed to MakerBot steadily losing their position and reputation as an industry leader, before getting absorbed by rival Ultimaker in 2022.
References
- ↑ https://blog.bambulab.com/firmware-update-introducing-new-authorization-control-system-2/
- ↑ https://all3dp.com/4/bambu-lab-limits-third-party-printer-control-with-new-security-update/
- ↑ https://bambulab.com/en-us/policies/terms
- ↑ https://blog.bambulab.com/firmware-update-introducing-new-authorization-control-system-2/
- ↑ https://blog.bambulab.com/firmware-update-introducing-new-authorization-control-system-2/
- ↑ https://old.reddit.com/r/BambuLab/comments/1i45iy2/bambu_lab_reserves_the_right_to_brick_your/
- ↑ https://old.reddit.com/r/BambuLab/comments/1i45iy2/bambu_lab_reserves_the_right_to_brick_your/m7sezlg/
- ↑ https://old.reddit.com/r/BambuLab/comments/1i45iy2/bambu_lab_reserves_the_right_to_brick_your/m7t8i7r/
- ↑ https://www.bitdefender.com/en-au/blog/hotforsecurity/someone-is-hacking-3d-printers-to-warn-owners-of-a-security-flaw
- ↑ https://www.csoonline.com/article/566223/over-3700-exposed-3d-printers-open-to-remote-attackers.html
- ↑ https://wiki.bambulab.com/en/security-incidents-cloud-traffic
- ↑ https://wiki.bambulab.com/en/software/bambu-connect
- ↑ https://forum.bambulab.com/t/full-non-cloud-based-network-option-needed/3643
- ↑ https://www.classaction.org/hp-printer-lawsuit
- ↑ https://www.wired.com/story/tesla-remote-disable-used-car-features/
- ↑ https://blog.bambulab.com/firmware-update-introducing-new-authorization-control-system-2/
- ↑ https://wiki.bambulab.com/en/software/bambu-connect
- ↑ https://wiki.bambulab.com/en/software/bambu-connect
- ↑ 19.0 19.1 19.2 https://www.facebook.com/BIGTREETECH/posts/pfbid0SNZGxvf7NRdmyVgHf6y9yNedNbU2RrCfdT8gugTSD4AYfr5BHneNF9H1EbwyYiJEl
- ↑ https://forum.bambulab.com/t/this-new-auth-system-will-make-me-sell-my-printers/135400/9
- ↑ https://blog.bambulab.com/firmware-update-introducing-new-authorization-control-system-2/
- ↑ https://forum.bambulab.com/t/bambu-studio-1-10-2-public-beta/134549/12
- ↑ https://forum.bambulab.com/t/full-non-cloud-based-network-option-needed/3643/9
- ↑ 24.0 24.1 https://x.com/fever_soft/status/1880630570809795034?t=qJyh4SGFZFllcYrqexGW-Q&s=19
- ↑ https://wiki.bambulab.com/en/software/bambu-connect
- ↑ https://github.com/SoftFever/OrcaSlicer/issues/8063
- ↑ https://forum.bambulab.com/t/this-new-auth-system-will-make-me-sell-my-printers/135400/9
- ↑ https://github.com/SoftFever/OrcaSlicer/issues/8063
- ↑ https://wiki.bambulab.com/en/software/bambu-connect
- ↑ https://forum.bambulab.com/t/bambu-studio-1-10-2-public-beta/134549/12
- ↑ https://public-cdn.bblmw.com/upgrade/bambu-connect/bambu-connect-beta-darwin-arm64-v1.0.4_4bb9cf0.dmg
- ↑ https://www.reddit.com/r/OrcaSlicer/comments/1i2t6l8/comment/m7tuf2i/
- ↑ https://github.com/ChazLayyd/Bambu-Lab-Klipper-Conversion
- ↑ DhazLayyd's Discord Community https://discord.gg/W6B5mBejuC
- ↑ https://github.com/SoftFever/OrcaSlicer/issues/8063
- ↑ https://forum.bambulab.com/t/this-new-auth-system-will-make-me-sell-my-printers/135400/4
- ↑ https://forum.bambulab.com/t/full-non-cloud-based-network-option-needed/3643/9
- ↑ https://forum.bambulab.com/t/bambu-studio-1-10-2-public-beta/134549/12
- ↑ https://forum.bambulab.com/t/full-non-cloud-based-network-option-needed/3643/5
- ↑ https://forum.bambulab.com/t/bambu-studio-1-10-2-public-beta/134549/4
- ↑ https://old.reddit.com/r/BambuLab/comments/1i2psvz/firmware_update_introducing_new_authorization/
- ↑ https://forum.bambulab.com/t/full-non-cloud-based-network-option-needed/3643/9
- ↑ https://forum.bambulab.com/t/bambu-studio-1-10-2-public-beta/134549/12
- ↑ https://www.trustpilot.com/review/bambulab.com?sort=recency
- ↑ https://forum.bambulab.com/t/full-non-cloud-based-network-option-needed/3643/5
- ↑ https://www.classaction.org/hp-printer-lawsuit
- ↑ https://hackaday.com/2016/04/28/the-makerbot-obituary/
- ↑ https://techcrunch.com/2014/05/28/makerbot-responds-to-critics-who-claim-it-is-stealing-community-ip/